Do you think your blog is secured? Wait until you read this.
I got a mail from one of my readers pointing this issue out on my blog. As a matter of fact, as a webmaster and php developer, it took me just negligence to not have gotten these leakages handled. With just a few clicks in your cPanels, these security flaws can be dealt with in a matter of minutes.
I tested over 5 blogs I read so often and non of them was safe. This is serious! How come almost everyone does not care about this yet we talk about safety here and there.
I’m sure these flaws are responsible for the thousands of hacks we have on WordPress these days. These leakages reveal key information about your web hosting. Hackers may now use these information to develop strategies to attack and bring down your blog.
NB: Read more on securing your blog from hackers
Vulnerability 1
Copy the link below and past in your address bar. Replace the https://yourdomainname.com with your real domain name:
https://yourdomainname.com/wp-includes/vars.php
What if your blog is installed in a sub-domain like this below:
https://comapanyname.com/blog/
This is what you should do:
https://comapanyname.com/blog/wp-includes/vars.php
Now validate this in your address bar. If you see the following screenshot, it means your server may be revealing critical information to the bad guys and if security on that server is not strong enough, getting it might just be a matter of time.
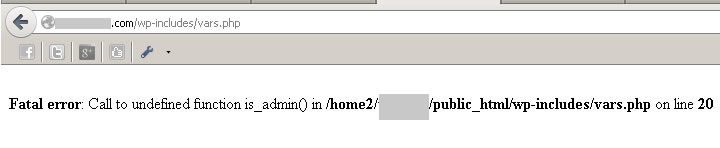 You see that the direct location of your files on the server is revealed. This makes the hacker’s job a bit lighter.
You see that the direct location of your files on the server is revealed. This makes the hacker’s job a bit lighter.
Proposed solution
My proposed solution is to ask the server to silent all errors. In other words, don’t show any errors to the screen. Let’s see how to do this in cPanel.
Log on to cPanel. Locate the “Software/Services” tab and click “php.ini Quick Config”
On the page that follows, carefully locate “display_errors” and turn it off as shown on the image below:
Click “Save Changes” button at the bottom of the page.
You may now go back to check to see if this works at https://yourdomainname.com/wp-includes/vars.php
Vulnerability 2
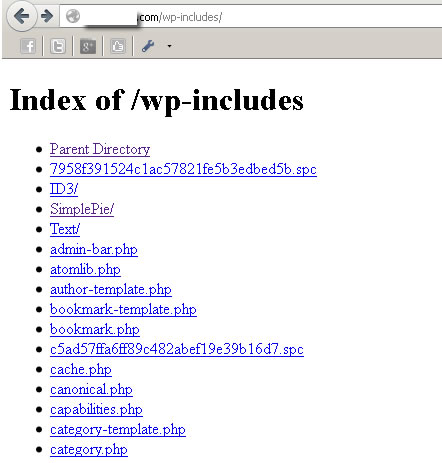
In this leakage, you are openly showing the listing of your files to everyone that cares to know. Let’s see if your files are being revealed:
Paste the following link in your address bar. Of course, you have to replace the portion yourdomainname.com with your real domain name
https://yourdomainname.com/wp-includes/
If you see a listing of your files, that means you’ve got work to do
Proposed solution
1 – > Create a blank index file (name it index.php) and upload in this folder to disable directory listing. If you go by this solution, you will have to do this for every directory you want to protect. I propose you go by solution 2 below
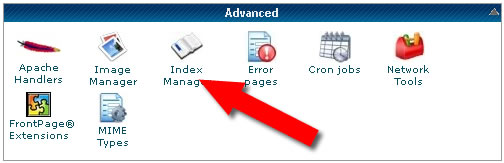
2 – > Locate the “Advanced” tab in your cPanel home page and click the “Index Manager” command:
NB: Your cPanel skin may be different from mine. So expect some differences in design.
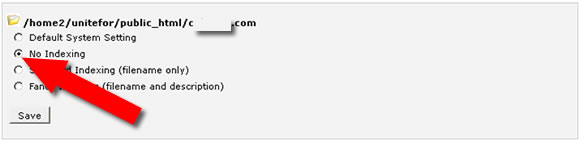
On the screen that follows, select the domain or folder you you wish to protect by clicking the name (not the icon).
Finally, click the “No Indexing” option on the list as shown on the image below and “Save” This will make sure people do not see the files in your directory and sub-directories.
If you go back to your link to test this out, you are surely going to see “ERROR 403 – FORBIDDEN” This is not sexy at all. In one of my subsequent posts, I’ll show you how to build and load your own error pages. Be sure therefore to join my list so you don’t miss it
NB: In issue 1 above where you turned error displays to OFF, be sure to revert to ON if you want to debug online.
If following these steps is an issue to you, be sure to contact me so we can work a way out
Let me hear from you in the comment below if this post has helped you in any way. Do also share this on social media so others may get to know about it 😉

Comments are closed.